Phishing protection for businesses is no longer a “nice-to-have.” It’s a critical necessity. In 2025, phishing remains the #1 cause of data breaches worldwide. Whether you run a startup or a large enterprise, your business is a target.
From fake login pages to spear-phishing emails that look frighteningly real, cybercriminals are constantly evolving their tactics. This guide outlines 10 actionable strategies for phishing protection that every business should implement right now.
1. Train Employees to Recognize Phishing Threats
Most phishing attacks start with a single click—usually from an employee who didn’t recognize a fake email. That’s why awareness training is the foundation of phishing protection for businesses.
Best practices:
- Offer quarterly cybersecurity training sessions
- Share real phishing examples and test staff with fake phishing emails
- Encourage reporting without punishment to build a strong security culture
🎯 Help your team spot threats before they click.
Explore Digital Identity Services →
2. Implement Multi-Factor Authentication (MFA)

Even if a hacker gains someone’s login credentials, MFA acts as a final barrier. It’s simple, low-cost, and incredibly effective for business-level phishing protection.
Why it matters:
- Blocks unauthorized logins even after password leaks
- Easy to roll out across cloud apps, email, and internal systems
- Now required under most UK data protection frameworks
🔐 Honour IT can implement MFA across your network fast.
Check our Managed IT Plans →
3. Use Enterprise-Grade Antivirus with Anti-Phishing Features

Antivirus isn’t just about viruses anymore. Today’s solutions provide real-time scanning of emails, attachments, and websites to block phishing attempts before damage is done.
Look for antivirus that offers:
- Email link scanning and malicious attachment blocking
- Cloud-based threat updates
- Endpoint protection across your full device network
🛡 See Honour IT’s professional-grade antivirus solutions →
View Antivirus Tools
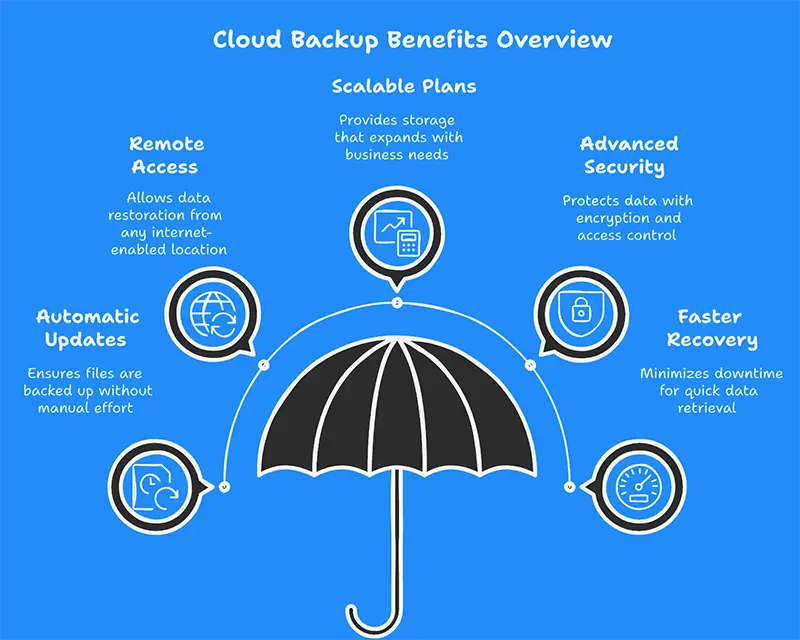
4. Set Up Secure Cloud Backup to Recover Fast
What if a phishing email leads to ransomware? What if files are deleted? Without proper backups, recovery can take weeks—or may never happen.
Why cloud backup is key to phishing protection for businesses:
- Keeps your data offsite and secure
- Enables fast restoration after an attack
- Protects business continuity, even during a breach
☁️ Stay protected with automated, encrypted backups.
See Cloud Backup Services
5. Block Malicious Emails with Advanced Email Filtering
Phishing emails can appear completely legitimate. Advanced filters are your first technical line of defense and a key part of any phishing protection strategy.
Smart filtering systems:
- Detect spoofed sender addresses
- Analyze email content and metadata
- Block known bad domains before users ever see them
Pair email filtering with awareness training to multiply your security posture.
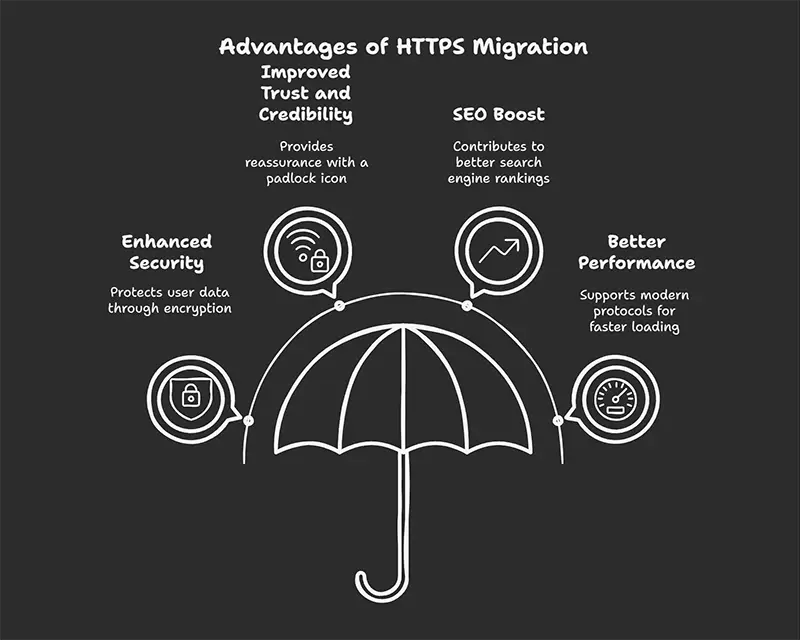
6. Monitor Domain Security and SSL Validity
Attackers often create lookalike domains like your-cornpany.com or use unsecured pages to trick users. You can avoid this trap with active domain monitoring and strict SSL enforcement.
What to do:
- Set up DMARC, SPF, and DKIM for email authentication
- Force HTTPS across your site
- Use monitoring tools to detect fake domain registrations
Bonus Tip: Buy similar-looking domain names and redirect them to your real site to block impersonators.
7. Create Clear Internal Security Policies
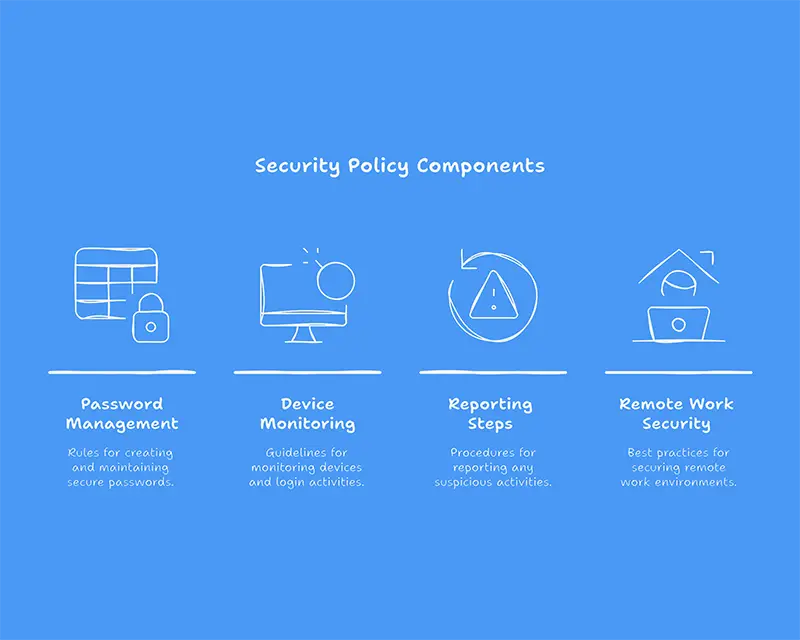
Security isn’t just about tools—it’s about people and behavior. Make sure your employees know the rules.
A good security policy should include:
- Password management rules
- Device and login monitoring
- Steps to report suspicious activity
- Remote work security guidance
These policies don’t just improve phishing protection for businesses—they raise your entire cybersecurity baseline.
8. Equip Browsers with Anti-Phishing Extensions

Phishing links aren’t just in emails. They can show up in Google ads, pop-ups, or fake websites. Modern browser extensions help detect and block threats.
Recommended tools:
- uBlock Origin
- HTTPS Everywhere
- Bitdefender TrafficLight
- Avast Online Security
Encourage your staff to use them on all work devices.
9. Run Regular Phishing Simulations
The best way to see how well your phishing protection for businesses is working? Test it. Send simulated phishing emails and track how your employees respond.
Benefits:
- Identify users who need extra training
- Track progress over time
- Discover real-time vulnerabilities
Use the results to refine your cybersecurity awareness strategy.
10. Partner with a Managed IT Security Provider
Let’s face it: phishing attacks are constant, evolving, and difficult to monitor 24/7. Most internal teams simply don’t have the time or expertise.
Why a Managed IT Partner like Honour IT helps:
- 24/7 monitoring and response
- Patch management and threat updates
- Professional support without in-house overhead
- Scalable plans that grow with your business
🧠 Let Honour IT handle your security while you focus on growth.
Get Managed IT Support
✅ Final Thoughts: Build Real Phishing Protection for Your Business
Phishing isn’t going away—but neither are your tools to stop it. Combine user education, strong policies, smart software, and reliable backup with expert IT support for true phishing protection for businesses in 2025.
The cost of prevention is nothing compared to the cost of recovery.
🔒 Let’s secure your business. Start your protection strategy today →
Book a free consultation with Honour IT