Are you looking to create a secure remote work environment for your UK business? In today’s digital age, remote work isn’t just a temporary measure—it’s a strategic shift that demands robust cybersecurity measures. Building a secure remote work setup is essential to protect sensitive data, maintain business continuity, and ensure regulatory compliance.
This comprehensive guide explains how to establish a secure remote work environment by implementing best practices, using state-of-the-art technologies, and leveraging expert IT support. With these strategies in place, your business will be better equipped to thrive while working remotely.
1. Understand the Risks and Challenges

The first step in building a secure remote work environment is recognizing potential security risks. Remote work introduces vulnerabilities such as insecure home networks, unmanaged devices, and phishing attacks aimed at remote employees. Key challenges include:
- Data breaches: With employees working from diverse locations, controlling data access becomes complex.
- Cyberattacks: Phishing and malware campaigns target remote workers more frequently.
- Compliance issues: Businesses must adhere to UK data protection regulations such as GDPR even when staff work remotely.
By understanding these challenges, your business can prioritize appropriate security measures to safeguard sensitive information.
2. Develop a Robust Security Policy

A clear, comprehensive security policy is the cornerstone of any secure remote work environment. This policy should outline acceptable usage, password protocols, data access procedures, and incident reporting.
Key components for a secure remote work policy:
- Password Management: Enforce strong, regularly changed passwords.
- Access Control: Use role-based access to restrict sensitive data to authorized personnel only.
- Incident Response: Establish a clear process for reporting and handling security breaches.
Implementing and regularly updating these policies ensures that all employees understand their roles in protecting the organization.
3. Enable Multi-Factor Authentication (MFA)
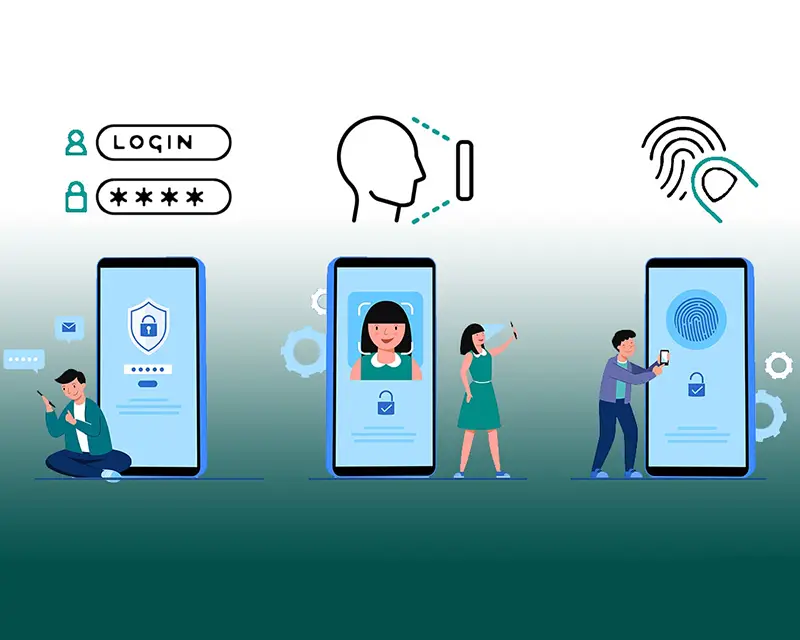
Multi-factor authentication (MFA) is a simple yet critical line of defence. Even if an attacker obtains a user’s password, MFA provides an extra layer of security by requiring an additional verification method.
Why MFA is essential for remote work security:
- It drastically reduces the risk of unauthorized access.
- It is simple to implement across cloud applications and remote systems.
- It meets regulatory requirements for data protection.
By integrating MFA into your security framework, you fortify your remote access channels effectively.
🔐 Boost your remote work security with Honour IT’s MFA solutions – View Managed IT Support Services
4. Secure Home Networks and Devices
Remote work environments rely on home networks, which are often less secure than business networks. Employees should be educated on securing their devices and networks.
Best practices include:
- Router Security: Encourage employees to change default router passwords and update firmware.
- VPNs: Use Virtual Private Networks to encrypt data transmitted between remote locations and the office.
- Device Protection: Ensure that all personal devices have up-to-date antivirus software, firewalls, and encryption enabled.
A secure remote work strategy must extend to all endpoints and networks employees use.
5. Leverage Cloud-Based IT Solutions

Cloud computing provides scalable and secure resources for remote work. Managed IT support providers can offer cloud-based services that safeguard data while allowing remote access.
Cloud solutions enhance remote work security by:
- Automated Backups: Protect your business from data loss in the event of an attack.
- Centralized Management: Monitor and update all endpoints from a central dashboard.
- Disaster Recovery: Enable fast recovery with secure, redundant data storage.
Cloud solutions not only improve security but also boost operational efficiency, making them a vital part of any remote work strategy.
☁️ Discover secure cloud backup and management services – Explore Cloud Solutions
6. Equip Browsers with Security Extensions

Phishing and malicious websites pose significant threats to remote workers. Equipping browsers with robust security extensions can help mitigate these risks.
Recommended browser tools include:
- Ad Blockers and Anti-Phishing Extensions: Such as uBlock Origin or Bitdefender TrafficLight.
- HTTPS Everywhere: Ensures secure connections on all websites.
These tools help employees avoid harmful sites and protect sensitive data during online activities.
7. Educate Employees Continuously
A secure remote work environment depends on an informed and vigilant workforce. Regular security training helps employees recognize phishing attempts, avoid unsafe practices, and adhere to company policies.
Training tips for effective remote work security:
- Schedule monthly cybersecurity webinars.
- Conduct simulated phishing exercises.
- Distribute clear guidelines and best practices.
- Encourage a culture of security awareness.
The more your employees know about threats, the better they can protect your business.
8. Monitor and Manage Remote Endpoints
Continuous monitoring of remote devices and networks is crucial to detect and respond to security incidents swiftly.
Consider these strategies:
- Endpoint Detection and Response (EDR): Tools that monitor, detect, and analyze threats in real time.
- Remote Management Software: Ensures that remote devices are regularly updated and patched.
- Log Analysis: Regularly review access logs and system alerts for unusual activities.
A proactive approach to endpoint management is key to maintaining robust remote work security.
9. Regularly Update and Patch Systems
Software vulnerabilities are a common target for cyberattacks, particularly in remote settings. Regular system updates and patch management are essential components of a secure IT infrastructure.
Steps to keep systems secure:
- Automated Updates: Enable automatic updates for operating systems, applications, and security software.
- Patch Management: Develop a routine process for applying patches promptly.
- Vulnerability Assessments: Regularly assess systems to identify and fix potential weaknesses.
Keeping systems up-to-date minimizes the risk of exploitation by cybercriminals.
10. Partner with a Managed IT Security Provider

For many UK businesses, building a secure remote work environment is too complex to manage in-house. Partnering with a managed IT support provider offers professional, round-the-clock expertise.
Advantages of outsourcing managed IT support:
- 24/7 Monitoring: Continuous oversight ensures quick detection and response to threats.
- Expert Knowledge: Access to specialists in cybersecurity, compliance, and cloud management.
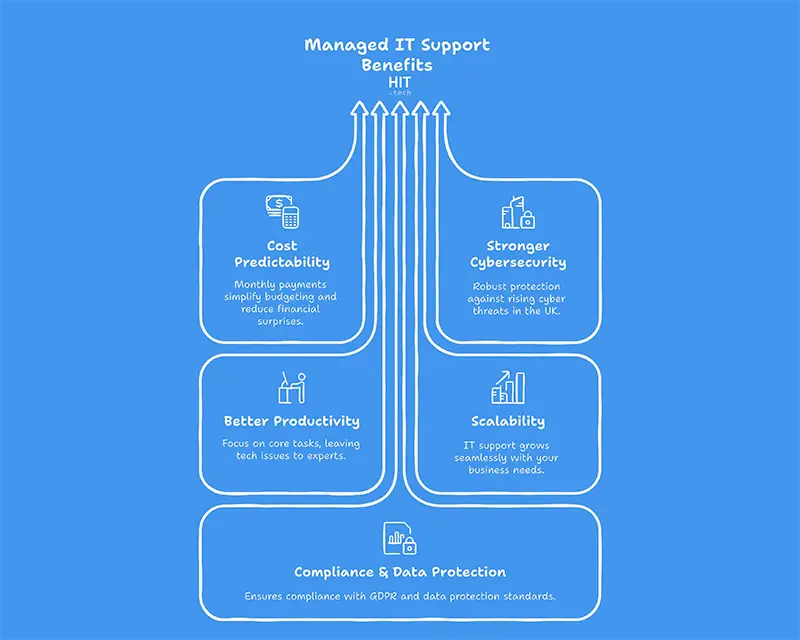
- Cost Predictability: Fixed monthly fees simplify budgeting.
- Scalable Services: Solutions that grow alongside your business needs.
By leveraging professional services, you ensure robust security and peace of mind.
🧑💻 Secure your remote work environment with expert support – Get Managed IT Support
Final Thoughts
A secure remote work environment is indispensable for modern UK businesses. By implementing robust cybersecurity measures—from MFA and VPNs to continuous employee training and managed IT support—you safeguard your data and maintain business continuity in an increasingly digital world.
Adopting these practices not only protects your assets but also builds trust with clients and partners, ensuring your business remains resilient against cyber threats.
🔒 Ready to enhance your remote work security?
👉 Visit our Shop to Explore IT Solutions